We’ve all seen the headline-grabbing figures on how much cybersecurity attacks cost each year, with some estimates put the figure at a staggering $10.5 trillion USD annually by 2025.
And then there’s the frequency attack happen — a UK government survey found 39% of businesses came under attack during Q1 in 2021.
But when it’s your organisation coming under attack, you’ll want to know you’ve done everything to minimise the possible damage. In this article, I’ll explore five common attack vectors and explain how G/On helps you proactively mitigate against the risk.
1. Mitigating account breaches due to phishing or account leakage
We've all seen and heard about recent data leaks from large company names and smaller companies like allekabels.nl in The Netherlands. The bottom line is that user passwords and usernames are available to an attacker.
Cybercriminals often steal user credentials to sell it on, resulting in anything from SPAM in your mailbox, targeted phishing attacks on select groups of users, right through to an attack on company systems because the user used the same password on different platforms.
Combining these credentials with 2FA improves the security level, but it doesn't yet give a 100% guarantee. I have seen cases where a company's acceptance environment did not use 2FA, so attackers managed to get access that way. And I don't even want to mention the different ways to circumvent 2FA.
In the Allekabels case, millions of captured encrypted passwords were not properly hashed/encrypted either, resulting in plaintext passwords. And it just so happens that many users place business orders here. You can imagine the consequences.
Telling users not to use the passwords for their company data elsewhere is a good policy and is frequently proclaimed in awareness training courses. However, there is no technical way to prevent it, so using only passwords (with 2FA) is no longer enough to mitigate the risks.
It is, therefore, indeed helpful to review your current authentication method. Consider not only the technique but also the tooling.
How G/On helps: With this in mind, we focused (years ago) on using safely stored certificates that can be used in combination with traditional credentials to gain access to company data. This approach enabled direct control over certificates, both fully automated and manually, and allows secure (even temporary) user access.
2. Reduce network breaches through infrastructure vulnerabilities
Recent months have seen a significant increase in network vulnerabilities, including Pulse Secure, Sonicwall, Netscaler and Cisco. The number of CVEs alone isn't the only concern; it's also the related risk score. Increasingly, the risk score per vulnerability found is more than 8 (max. 10).
How G/On helps: G/On does not use the infrastructure functionality at the higher layers of the OSI model. Any vulnerabilities in the network infrastructure do not impact the desired security level of G/On and the functionality it provides.
As a result, these weaknesses cannot directly lead to unauthorised access to internal company systems - which in most cases leads to ransomware attacks or a data breach. It's certainly not the case that G/On will prevent data breaches. But the risk of a data breach through misusing VPN portals etc., is drastically reduced.
3. Prevent vulnerabilities in internet-facing applications being exposed
We’ve all heard news stories about companies brought down by ransomware attacks - these attacks impact all of us, not only people working in IT security. Recent cheese shortages at Dutch supermarket firm Albert Heijn are a case in point.
The truth is, vulnerabilities will always exist. Tackling them comes down to investing in a good vulnerability management platform. Then weaknesses, even in network configurations, can be quickly spotted and remedied. In addition, a good security infrastructure design will always take into account a breach and limit the impact of any vulnerability.
How G/On helps: G/On focuses on limiting the visibility of these applications — and, therefore, the unavoidable associated vulnerabilities. Applications are only visible to the legitimate user and certainly not exposed to the internet. Direct access to the applications is controlled within the G/On Manager, using the ZeroTrust model.
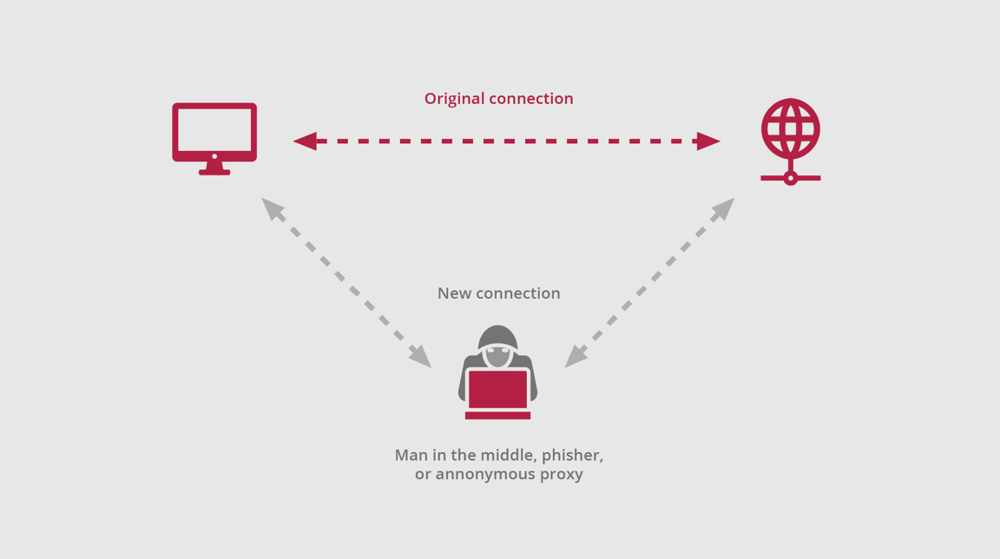
4. Stop "Man-in-the-Middle" Attacks
Man in the Middle (MiTM) attacks are not a new cybercrime, but they still result in costly data loss.
The number of MiTM attacks has increased in recent years. Scenarios like employees accessing company data on devices via unsecured or public Wi-Fi networks combined with
relatively easy-to-access tools have made it a popular and relatively easy form of criminal activity.
How G/On helps: As G/On uses an encryption protocol with mutual authentication based on certificates, it is therefore certain that the endpoints are never different from what they declare. A technique like MITM is not possible with G/On.
5. Not synchronised identity store
When user access is controlled in multiple stores, it’s easy for them to get out of sync. Over time, when people leave and join the organisation, changes roles or move departments, changes in their access permissions, things get missed, and changes aren’t universally made. Essentially it means some users can end up with the wrong access privileges.
How G/On helps: G/On provides a single central point where authorisation for applications is organised. However, G/On can use multiple IdPs for this: Access to applications can be managed per user. Revoking rights and changing access times can also be managed there, so there’s no longer a risk that the user can access the platforms through another application.
Secure by design
G/On is a scalable and secure remote access solution built on zero-trust principles. It decreases your attack surface, increases visibility into user activity and reduces complexity. Plus, it delivers additional business benefits like BYOD, fast installation, scalability, affordability, permission access and a stable connection with no bandwidth issues.
G/On is simple for IT to implement, manage and control. It does not use VPN, but it can also work alongside your current VPN or existing solution to enable business and support effective remote working.
And more importantly, the users working with G/On will have an experience as if they were working in an office. Except for the coffee!
But don’t just take our word for it. See it in action Request a Demo.



